Trust ID platform
Secure AWS cloud infrastructure development
A highly secure cloud infrastructure developed for an identity verification platform.
"I wouldn't hesitate in recommending Codevate to support the design and build of your web application or cloud platform, they are experts in their field and also understand the value of implementing security within the development lifecycle – which is a real advantage for clients."
Rebuilding a secure cloud infrastructure
The Trust ID platform is a secure identity verification platform, dealing with highly sensitive personal documents over the Internet. A highly secure infrastructure was required to host and protect the software and its data, both in transit and at rest.
Our client had their pre-existing software hosted on AWS. An initial security audit highlighted a large number of issues with the existing infrastructure. Their existing team, made up of employees and contractors, did not have the capability to deliver a secure infrastructure to the required standard.
With our virtual CTO service, we become a core part of both the development and management teams. The infrastructure we developed passed a strict security audit and penetration test, allowing our client to work with the nuclear sector.
Want to build your own cloud infrastructure?
Services delivered
- Technical evaluations of pre-existing infrastructure & software
- Consultancy
- DevOps and infrastructure
Technologies used
- AWS cloud infrastructure
- Terraform
- Ansible + Packer
- Docker
Highlights of secure cloud infrastructure
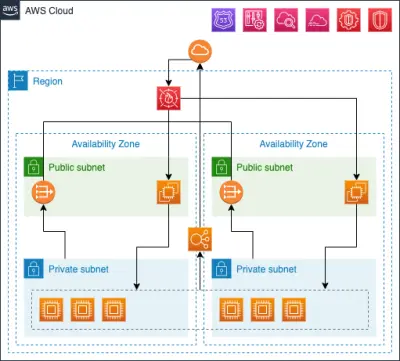
Secure AWS infrastructure
- Audit logging - full trail of access, keeping track of exactly who accessed data and systems, or made changes to them
- Strict access control - principle of least privileged used to give minimal access to all parties to reduce the potential damage from a compromised account or bad actor
- Highly secure - access from the outside world was extremely limited and regulated, reducing the changes of a remote attacker getting in - and limited what they could do in the event they did
- Monitoring and alerting - allowing the team to instantly become aware of intrusion, performance issues, service outage, etc.
Infrastructure-as-code
- Industry best practice - software development best practices (version control, documentation, etc.) can be applied to infrastructure with this approach
- Fully documented - the entirety of the infrastructure is documented as code, making the infrastructure immediately reproducible
- Changes can easily be audited - as all changes are documented, they can be reviewed by other parties before being applied
- Secure - even those working on the infrastructure implementation do not need to access to production systems and data
Consultancy and technical evaluations
- Technical evaluation - we audited the pre-existing software, identifying security issues before the external audit, saving on costs and the risk of missing the deadline
- Helped manage team of external contractors - to ensure the project was delivered on time and within budget, including investigating contractor performance concerns
- Acted as CTO (Chief Technical Officer) - with a retainer in place to guarantee availability, we were always available to provide advice and consultancy when needed
- Produced technical guidelines - covering work processes, coding standards, testing, etc. to help standardise work quality from all parties involved
Behind-the-scenes and other top features
Not all heroes wear capes. These behind-the-scenes features don't have screenshots, but form an important part of the project.
Full architecture specification
Ensured that the security criteria would be met before investing in implementation.
Infrastructure running cost estimation
Detailed cost estimation allowed cost-benefit evaluation.
Multi-server auto-scaled architecture
Infrastructure scaled across multiple availability zones to reduce the risk of service outage.
Separate deployment environments
Development, staging, and production environments to support quality assurance and limit access to production.
Want to develop a secure cloud infrastructure like?
"I wouldn't hesitate in recommending Codevate to support the design and build of your web application or cloud platform, they are experts in their field and also understand the value of implementing security within the development lifecycle – which is a real advantage for clients.."
- 100% UK-based
- Complimentary scoping call
- At-a-glance feasibility analysis
- No obligation high-level proposal
- Work with an expert to evolve your idea
Project outline: rebuilding the secure cloud infrastructure
The client had their pre-existing identify verification software hosted on AWS. The software dealt with highly sensitive personal documents, submitted via the web and a mobile app. In order to secure a large contract in the nuclear industry, the platform needed to pass a thorough security audit and penetration test to gain certification.
An initial security audit was undertaken, which highlighted a large number of issues with the existing infrastructure. The client's existing team, which included employees and external contractors, did not have the capability to deliver a secure infrastructure to the required standard.
The client also did not have a technical lead, making managing a disjoint technical team very challenging. This situation made it very easy for contractors to take advantage, as they had to be taken at their word, with their work going unchecked.
The back-end software was quite large and complex, being made up of a number of services and microservices - a lot of moving parts. As is commonly seen in start-up environments, documentation and code quality suffered.
Our involvement
We became a core part of both the management and development teams, acting in the capacity of CTO/head of technical as well as in a hands-on capacity. Initially, we performed technical evaluations on the existing infrastructure and software, to take stock of the situation. From there, we put together a detailed specification for a new infrastructure that would meet the security, as well as performance, requirements. We found multiple issues with the software and worked closely with the developers to rectify them. Various modifications to the software were required for it to be compatible with a modern infrastructure.
In parallel to the infrastructure design and development, we were providing consultancy to the non-technical management. Not only the new infrastructure was required, but there was also an ongoing software development effort. This involved helping to manage the various parts of the development team, to ensure the project was delivered on time and in budget.
Once the specification was signed off, we built a greenfield AWS infrastructure using best practices, securing it to high standards.
Delivering the new infrastructure
With our new infrastructure and our involvement in improving the software, we successfully passed the strict security audit and penetration test, allowing the client to achieve its certification. Performance bottlenecks were also improved with the new infrastructure, improving the usability of the software.
Now that the infrastructure is in place, it is largely self-sustaining and requires little maintenance. Monitoring and alerts are in place to let the client's team of performance problems, security breaches and service outage.
After the delivery of the project, the ongoing consultancy retainer was kept in place to help the company manage and grow its internal development team.
Want to build your own secure cloud infrastructure?
Looking to develop software that's greater than the sum of its parts?
Send us a message

